In a recent demonstration, a team of white hat hackers showed how an attacker can compromise the corporate security with the help of easily available equipment bought from Amazon and eBay. This was possible due the lack of encryption in the data transmission process.
reaking into a corporate office without much hassle is easier that thought. The same was recently demonstrated by a team of white hat hackers who broke into the main office of a power company in the Midwest.
Summing up the hack in two lines, here’s how it happened: The hacker uses a fake employee badge and waves it at a sensor. As a result, the door unlocks with a fake card with the help of some stolen data.
After entering the building, the hacker looks at the desk of some employee and installs a custom hardware. Later, they compromised other electronics equipment and got access to confidential documents.
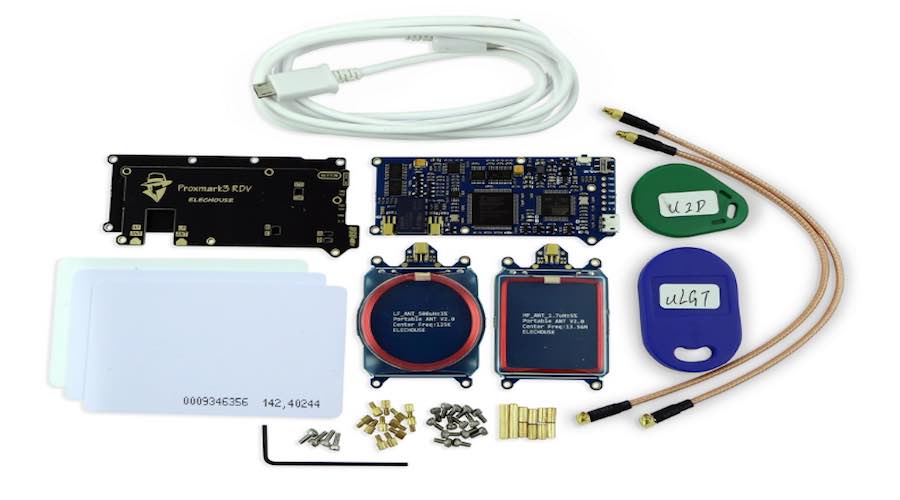
This was possible due to the fake badges with nothing more than $700 worth of equipment to steal badge data. “Yeah we got the big, long range reader from Amazon,” said Matt Grandy, the security consultant for RedTeam Security. “They’re also all over on eBay.”
He carried around the badge reader in his bag and grabbed card data from three feet away, storing it on a microSD card.
This team of white hat hackers made this hacking look easy by exploiting a well-known flaw with RFID (radio-frequency identification) — a common method of authentication in facilities. Most of the time, the data is transmitted without any layer of encryption, giving someone a chance to grab the data and make a clone employee’s card.
To grab the data from an employee, a hacker can easily put the RFID reader in some bag and go near an employer, grabbing his badge data out of the thin air. Later, with a device called Proxmark, the data is written to a new card.






No comments:
Post a Comment